3 Reversing Challenges - HackTheBox
- Idan Buller

- Jan 31, 2021
- 2 min read
Updated: Feb 1, 2021
HackTheBox: Baby RE [by Xh4H]

File Type: exe
Level: easy
This is the first challenge in this series and it is super basic. After downloading the executable named (baby.exe) we should give it the appropriate permissions to run by typing
chmod +x babyThen, running the executable will print this output to the terminal –
Now, when the executable asks for “secret password”, we may find it inside the code itself, and sometimes we won’t even need to use a decompiler.
To solve this challenge we only need strings.exe, which is part of SysInternals and allows us to scan the file we pass through in order to UNICODE strings of a default length of 3 or more UNICODE characters.
Inside the strings, we can find the matchable key “abcde122313”. Don’t get confused with the HackTheBox key presented in the output. We are getting the correct key after typing the correct executable key –
HackTheBox: Bypass [by Baikuya]

File Type: exe
Level: easy
The second challenge is a little bit fancier. After downloading the executable named (bypass.exe) we should give it the appropriate permissions to run by typing –
chmod +x Bypass.exewhen running the executable, we need to insert username + password and hopefully get the key. But, this time strings.exe will not be our rescuer but only the first step to solving this challenge –
We can find more information about the executable such as the libraries it is using, but still, we can’t get the key.
Now, after we realized that this executable needs to be analyzed dynamically, we will send it to the lovely
Immunity Debugger (https://www.immunityinc.com/products/debugger/) –
Open Bypass.exe inside the debugger and make sure the file is running, then insert some strings into the input –

Next, search for the address you wrote the string and follow the dump. Then, we can explore through it and search for what we can find –
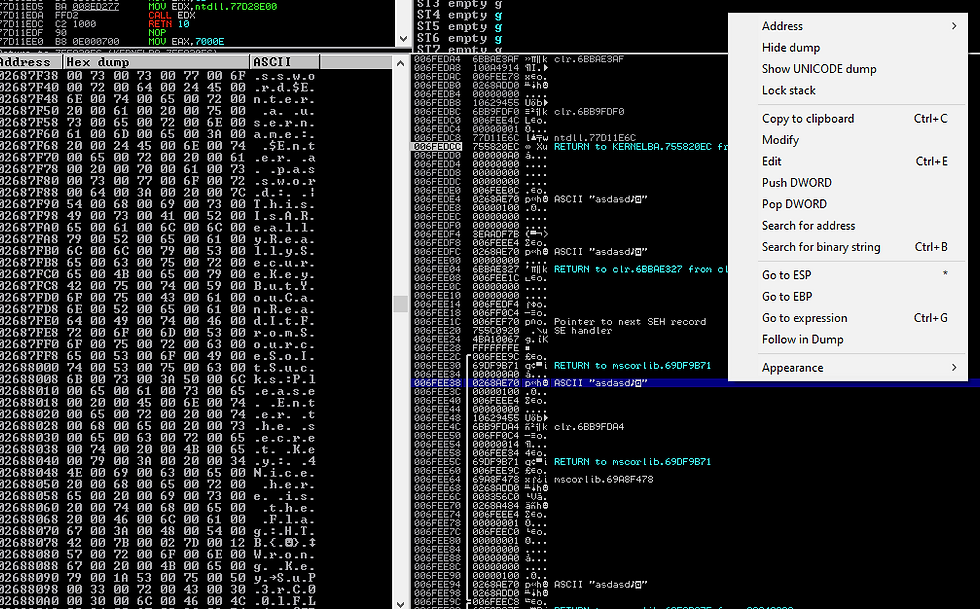
In the dump, we will find the output HTB{SuP3rC00lFL4g} –

HackTheBox: Impossible Password [by decoder]

File Type: exe
Level: easy
The third, in my opinion, is might be the hardest of the tree, but not so complicated. All we need to do is to use the “framework for reverse-engineering and analyzing binaries” – radare2.
At first, when we run the file (which is not executable, but a .bin file) after we gave it the appropriate permissions (chmod +x) we don’t get any output which gives us a hint –
So, we will explore it dynamically with radare2 –
Then we can see the first step is to insert the first key: “SuperSeKretKey”, and the following byte sequence (A]Kr=9k0=0o0;k1?k81t) which encrypted with xor cipher we can get from the [fcn.00400978] value, which reflects our encrypted string at the end of the file -
So, the XOR cipher is 9 (0x9), we have the string, all that's left is to decrypt and get the key.





Comments