TryHackMe: The Marketplace Walkthrough
- SecHive

- Oct 29, 2020
- 4 min read
Updated: Oct 31, 2020


Title: Wonderland
Info: Can you take over The Marketplace's infrastructure?
Difficulty: Medium
Created by: jammy
Intro
'The Marketplace' is a wonderful machine with lots of interesting things to learn.
You have to implement a cookie stealer, SQL injection, and finally escalate two times, which include wildcards injection and using a docker privesc method that will allow us to obtain the user and root flag at the end.
Scanning and Enumeration
Nmap Scan Results:
We found 3 ports (22, 80, 32768) open for this machine. We can also see a page /admin which disallowed in robots.txt, and a strange port running Node.js (Express middleware).
Let's move on to see is there is more interesting pages with gobuster
Gobuster Scan Results:
Next, I went to the website and found no differences between port 80 and port 32768 that we found earlier. The site looks exactly the same with the same functionality. On the home page, we can notice 2 users who posted items - michael and jake.


An initial investigation of the site and source code led me to a registration page where you can easily register, and then connect with the user I chose.
I kept looking at the site and there is a "New listing" page where you can post an item, and there I immediately saw that there is an ability to upload files but it is disabled. Simply using Inspect Element I deleted the relevant attribute and tried to upload an image file to find out if there are any file-size / file-extension restrictions and if I can manipulate to get a reverse shell. Uploading files here are meaningless the file was not sent to the server in request at all.
Ok, so I tried to perform basic XSS and it was pretty easy, it worked right away.
The next step was to think about how could I make it my advantage over other users on the site. I saw that every item that goes up on the site has an option to report to the administrators and here I realized that I could exploit the vulnerability, to try and steal the cookies from the administrators.
Exploitation - XSS
For this purpose I used the following tool for stealing cookies:
Steal Cookies with Reflected XSS https://github.com/s0wr0b1ndef/WebHacking101/blob/master/xss-reflected-steal-cookie.md
Just run the command to start an HTTP server at port 8888 (default for this tool, you can change whatever you like):

Create a New listing with XSS payload (alert box will not work here, don't use it), and report listing to admins
Note: the first cookie you will receive is probably yours (look at the IP) and then the administrator cookie will arrive from the server. If for some reason you did not receive a cookie after a few moments, report again the item to admins.
Note 2: In the below screenshot the machine was terminated so the IP was changed.
BOOM! We got administrator cookie.


Using CookieManager (Cookie Editor)
or press F12 → Storage → Cookies replace the cookie value and refresh the page.
On the admin page, we can grab flag 1 and see the registered users of the site, michael and jake are admins.

Exploitation - SQL Injection
Identify whether an application is vulnerable to SQL injection
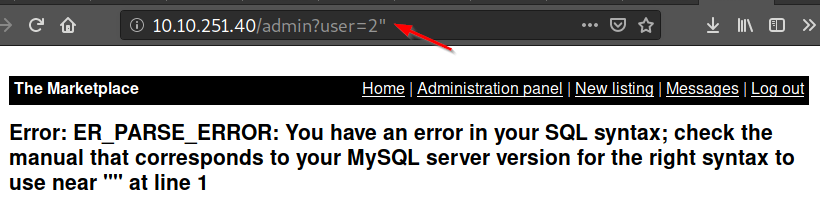
When I visited the user's page I could notice the parameter /admin?user=2 at the URL. I wrote quotes after the digit and it seems that an SQL error is obtained, which indicates that we have a good chance of SQLi
/admin?user=2"Find out how many columns the current table has
If the number that we pass in the parameter is less than the total number of columns in the current table, the output of the application should not change because the SQL query is valid. However, if the number is larger than the total number of columns, we will get an error because there is no such column. In our case, we have identified 4 columns because at 5 we get an error.

See which column is vulnerable
Now that we know how many columns the current table has, we will use UNION to see which column is vulnerable. UNION SELECT is used to combine results from multiple SELECT statements into a single result. The vulnerable column is the one whose data is being displayed on the page.
Note: put dash '-' before parameter
We can confirm this by replacing it with version() which will show the MySQL version
Find the table names
The group_concat() function concatenates results into a string. The Information_schema is a database that stores information about other databases. The database() function returns the name of the current database.
We got the following tables: items, messages, users

Find columns
Same method like above

Output is in the same order:
items: id,author,title,description,image
messages: id,user_from,user_to,message_content,is_read
users: id,username,password,isAdministrator
Now, we will retrieve the desired sensitive information
First and foremost I tried to get the passwords of the users. what we get is the hash of each user. To save you time, this is a bcrypt Blowfish hash, and it is rabbit hole and uncrackable (don't bother).
So I kept searching and got a message at system user (id=1), and got the password for SSH which turns out it's jake's password


SSH creds:
jake:@b_ENXkGYUCAv3zJconnect & get flag 2 (user.txt)
Privilege Escalation
So when I went to check if jake can run sudo commands, I saw that there is a path to backup.sh file and there is an option to run it without a password in the name of michael. Examining the contents of the file, it appears that it backs up the entire folder and uses the '*' symbol to include all the files in the folder.

Exploiting Wildcard
In the following article, we will cover “Wildcard Injection” an interesting old-school UNIX hacking technique: https://www.hackingarticles.in/exploiting-wildcard-for-privilege-escalation/
In our case, where is no cronjob running so we manage it manually.
Generate netcat reverse shell malicious code
Open netcat listener
Copy the generated payload and paste inside the victim’s shell

Spawning a TTY Shell
More information about TTY: https://netsec.ws/?p=337
I like this one: (not shown in the url above)
Get Root user
michael in docker group which running as root, so we will go to GTFOBins:






















Comments